On 16 December 2020 the following joint statement was issued by the FBI, the Cybersecurity & Infrastructure Security Agency and the Office of the Director of National Intelligence: “Over the course of the past several days, the FBI, CISA, and ODNI have become aware of a significant and ongoing cybersecurity campaign.”
What’s been widely labelled as the SolarWinds attack was presumably the longest-lasting, most sophisticated and impactful penetration of the global IT infrastructure.
Others called it a digital 9/11.
What the heck happened and why should we care?
In a 14 December 2020 SEC filing, SolarWinds Corp described the features of the hack, a so-called supply-chain attack. A presumably state-sponsored cyber foe managed to compromise the software build system of its Orion platform. This system is an automated tool to create software (and updates) by compiling (translating) source code into machine-digestible binary code, packaging binary code and running tests (debugging).
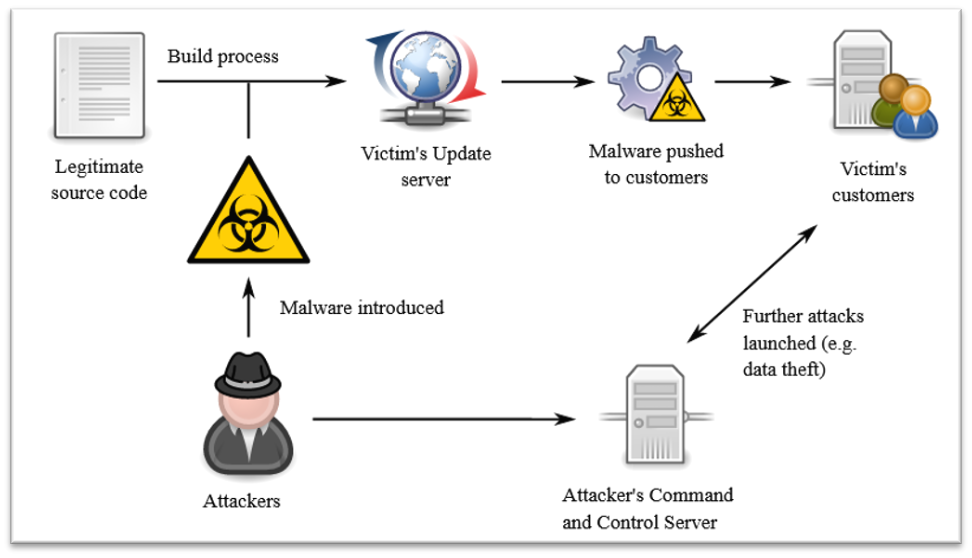
During the course of the attack intruders added malicious code, a so-called backdoor, into one of Orion’s platform updates released to and installed by SolarWinds Orion customers around the world between March and June 2020. This backdoor enabled third parties to siphon off data and/or insert malware into the customer’s software applications. The features of the hack (small footprint, in-country IP disguise, digital signatures etc.) indicate highly sophisticated actors.
What is the SolarWinds Orion platform being used for?
SolarWinds marketing folks describe it in a nutshell as follows: “One vendor. One platform. One single pane of glass.” (One is inclined to add: One single point of entry!)
Looking closer, the platform acts as a one-stop-shop to monitor and manage an organisation’s entire IT environment comprised of its physical, virtualised and cloud IT components.
For organisations using the Orion platform this is like losing not just a single key, but an entire key chain, resulting in universal access not only to your house, but also the safe and every locked drawer
Orion’s most critical components include network, server and application monitoring, network configuration, log analyser (the what, who and when), VoIP network management (call traffic), server configuration, database performance analytics and automated (Microsoft) patch management.
Let’s take this in for a moment and consider the implications. In order to provide this level of service, Orion is granted almost universal access rights to its clients’ IT infrastructure and data.
Hence, a third party gaining access to Orion through a trusted software update service, is for organisations using the Orion platform like losing not just a single key, but an entire key chain, resulting in universal access not only to your house, but also the safe and every locked drawer.
Who’s been affected by the hack?
With worldwide customers in 190 countries including 499 of the Fortune 500 and numerous government organisations, SolarWinds’ customer list reads like quite a who’s who. Apart from the Pentagon, the National Security Agency, the Federal Reserve and the White House, it includes corporate heavyweights like Cisco, Credit Suisse, Lockheed Martin, Microsoft, Dow Chemical, Volvo, Siemens, PwC, E&Y and many other large multinational corporations. For obvious reasons only a handful of organisations, like the US Treasury and Microsoft, have acknowledged their exposure.
What does this all mean for those affected?
Well, apart from the obvious strategic importance of gaining undetected access to major government agencies for more than half a year, the economic fallout for corporations and financial institutions could potentially be devastating. Corporate intelligence/IT is probably working overtime to limit the fallout, which may range from large-scale identity theft all the way to product infringements and capital market manipulations.
What are the implications for the current data-driven proptech wave?
When thinking about cybersecurity, the proptech world typically distinguishes between data security and potential privacy breaches as well as vulnerabilities in internet-of-things (IoT) devices and related hardware and software. In a proptech context the IoT relates to an array of connected devices used to automate data capturing, building functions, property management and control.
Examples include access control using biometric data such as fingerprints or iris scans while IoT hardware applications used for property management relate to essential building functions like HVAC and elevator operations.
Let’s start by looking at potential data and privacy infringements. As a proxy for the myriad of proptech innovations out there, let’s look at two of Pi Labs’ investments in order to get a better understanding of the scope of collected data and associated privacy concerns.
Askporter is an AI-driven property management solution providing, among other things, tenant qualification and rent collection. These involve extensive personal data, credit scores, employment data, social security IDs and payment behaviour. Another application, Trussle, provides mortgage broker services, collecting a variety of personal, credit scoring and employment data.
For the second bucket, IoT devices, it’s helpful to take a look at the full technology stack involved.
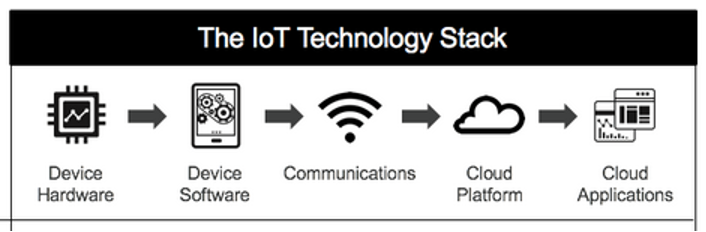
IoT proptech solutions range from relatively simple ones like security system embedded smoke detectors to more complex ones such as AI-enabled and usage dependent elevator controls.
Where does the relevance of the SolarWinds Orion hack come in?
Collecting and processing personal data by mortgage brokers or property managers isn’t really new. Compared with the more traditional ways, though, the new crop of proptech uses structured data and proprietary code which, if infiltrated somewhere along the supply chain, is easier to penetrate. Hence, siphoned-off data is easily misused to, for instance, perpetrate identity theft. The inherent growth model of tech companies also leads to increased data aggregation, which in turn multiplies vulnerabilities compared with data maintained offline or in unrelated or distributed systems.
IoT devices on the other hand use a variety of sensors as part of their data acquisition module to capture, process, digitise, analyse and transfer data to a centralised (cloud) storage.
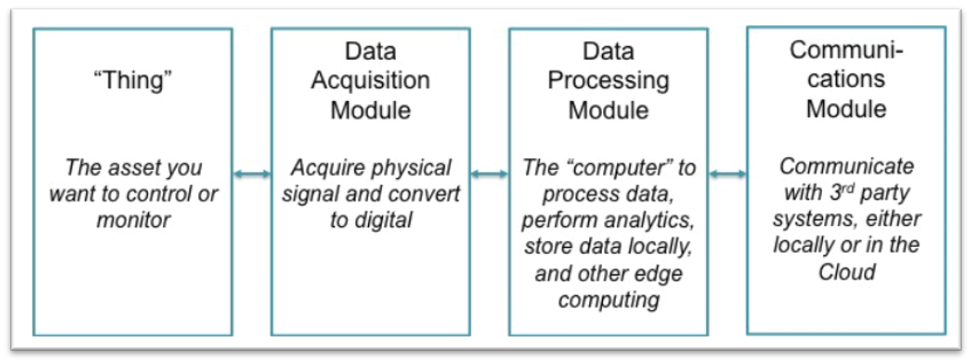
There are various supply-chain attack routes available to manipulate IoT devices. Hardware-related attacks could manipulate the chipset used within the IoT sensor to allow unauthorised access. Software-related attacks may infiltrate the on-chip processing or communication software by attacking the respective suppliers. Another route would be to infiltrate the (5G) connectivity (router attacks) used to transfer IoT data into cloud storages for further processing.
A recent case, where IoT devices used at a water treatment plant in Oldsmar, Florida, to regulate the drinking water’s sodium hydroxide content were manipulated, is a primary example for the level of risk involved. The back door used in this case came through TeamViewer, another (remote) IT management tool integrated with SolarWinds platforms.
What needs to be done?
Data and IoT device security needs a ‘seat at the grown-ups table’ in every organisation.
IT supply chains need to be transparent, subject to regular audits and penetration tests.
General (prop)tech competence needs to be elevated within organisations.
The proptech industry needs to take a page from the zero-tolerance approach used in health and safety policies of major contractors.
Be paranoid! There are many more SolarWinds out there. It’s just the beginning.







